Que no se descargue por completo. Se me dificulta escuchar claro a las personas que me llaman al celular. Suena muy baja la voz. Algunos modelos de celulares tienen dichos controles en la parte lateral. Es normal que a medida que el equipo se usa se vuelva lento. Elimine programas que no usa. Quite programas del inicio de Windows. Escriba en esa ventana 'msconfig' y luego Aceptar. Desfragmente el disco duro. En Windows Vista la ruta para activar esta herramienta es igual.
Combine palabras y letras. Ofrece 5 GB de capacidad gratis. Ofrece 50 GB de capacidad gratis. No puedo hacer llamadas por Internet. Siga los pasos del tutorial. De otro lado, mantenga activo el firewall de Windows.
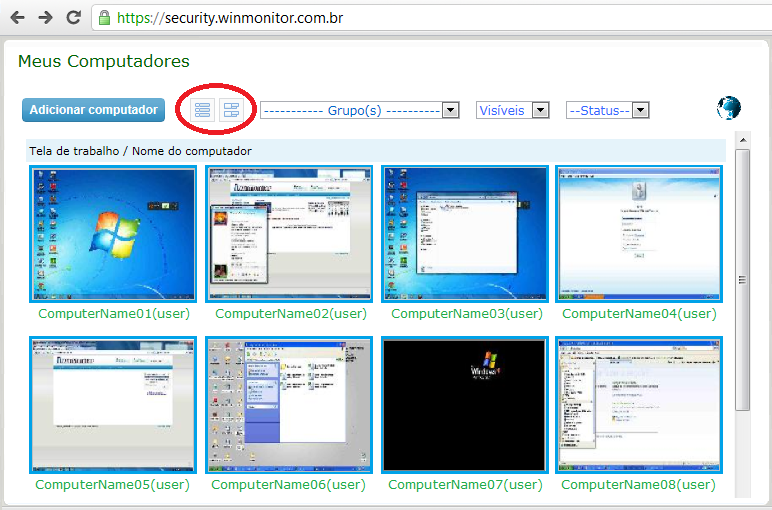
Convierte tu PC en una cámara de vigilancia - Atajos Web | Blogs | Peru21
Para protegerse puede usar varios programas 'anti-zombie'. Si ya eres suscriptor del impreso. A programming language that offers dynamic characteristics e. This is not a virus, but a trick that aims to make users believe they have been infected by a virus. A network of interconnected computers in a reasonably small geographical area generally in the same city or town or even building. These are parts of a web page, e-mail or document text, images, buttons, etc. This is a type of virus that modifies the address where a file is stored, replacing it with the address of the virus instead of the original file.
As a result, when the affected file is used, the virus activates. After the computer has been infected, the original file will be unusable. This is a program that appears quite inoffensive, but which can carry out damaging actions on a computer, just like any other virus. A set of commands or instructions carried out by a program repeatedly until a certain condition is met.
A macro is a series of instructions defined so that a program, say Word, Excel, PowerPoint, or Access, carries out certain operations. As they are programs, they can be affected by viruses. Viruses that use macros to infect are known as macro viruses. A virus that affects macros in Word documents, Excel spreadsheets, PowerPoint presentations, etc. This term is used to refer to all programs that contain malicious code MAL icious soft WARE , contain malicious code, whether it is a virus, Trojan or worm.
This is the action of assigning a shared network disk a letter in a computer, just as if it were another drive in the computer itself. Messaging Application Program Interface. A system used to enable programs to send and receive e-mail via a certain messaging system. This is a 32 bit number that identifies an IP address in a certain network.
A fundamental characteristic of a virus. This is the way in which a virus infects a computer. This is the way in which a virus spreads from one computer to another. This is the integrated electronic heart of a computer or IT system e. This is the set of specifications that allows text and files with different character sets to be exchanged over the Internet e. A peripheral device, also known as MOdulator DEModulator, used to transmit electronic signals analogical and digital.
It is designed to enable communication between computers or other types of IT resources. It is most often used for connecting computers to the Internet. This operating system , which predates Windows, involves the writing of commands for all operations that the user wants to carry out. A server for storing data, which is compatible with SQL Server This is an organized mail system that receives messages and distributes them to the recipients. MTAs also transfer messages to other mail servers. Exchange, sendmail, qmail and Postfix, for example, are MTAs.
This is a characteristic of a particular type of sophisticated virus, which infects computers by using a combination of techniques used by other viruses. Some viruses can use a mutex to control access to resources examples: By doing this, they make it difficult for antiviruses to detect them. Group of computers or other IT devices interconnected via a cable, telephone line, electromagnetic waves satellite, microwaves etc , in order to communicate and share resources.
Internet is a vast network of other sub-networks with millions of computers connected. An Internet service through which various people can connect to discuss or exchange information about specific subjects. A nuke attack is aimed at causing the network connection to fail. A computer that has been nuked may block. Person or program that launches a nuke attack, causing a computer to block or the network connection to fail.
A standard for embedding and attaching images, video clips, MIDI, animations, etc in files documents, databases, spreadsheets, etc. It also allows ActiveX controls to be embedded.
- gps de celular como rastrear!
- Un muro infranqueable contra los virus.
- 18 respuestas.
- localizar celular sony xperia z1.
- localizar mi celular microsoft.
System for subscribing or registering via the Internet as a user of a product or services in this case, a program and associated services. This is the action that certain programs or viruses take when they write over a file, permanently erasing the content. A program -or network connection- used to offer services via the Internet usually file sharing , which viruses and other types of threats can use to spread.
An operation in which a group of files or just one are put into another file, thus occupying less space. The difference between packaging and compression are the tools used. For example, a tool called tar is normally used for packaging , while zip or gzip -WinZip- are used for compressing.
A variable piece of data indicating how a program should behave in any given situation. Each partition of a hard disk can have a different operating system. An area of a disk containing information about the sections or partitions, that the disk is divided into. This is a sequence of characters used to restrict access to a certain file, program or other area, so that only those who know the password can enter.
COMO RECONOCER SOFTWARE ESPIA Y ELIMINARLO CON CODIGO CMD
A program that obtains and saves confidential data, such as user passwords using keyloggers or other means. This program can publish the list, allowing third-parties to use the data to the detriment of the affected user. A pocket-sized, portable computer also called palmtops. Like other computers, they have their own operating system , have programs installed and can exchange information with other computers, the Internet, etc.
Well-known brands include Palm, PocketPC, etc. This is the process that some antivirus programs carry out of continually scanning any files that are used in any operations albeit by the user or the operating system. Also known as sentinel or resident. Phishing involves massive sending of emails that appear to come from reliable sources and that try to get users to reveal confidential banking information. The most typical example of phishing is the sending of emails that appear to come from an online bank in order to get users to enter their details in a spoof web page.
Refers to an operating system , in a specific environment and under certain conditions types of programs installed, etc. A technique used by viruses to encrypt their signature in a different way every time and even the instructions for carrying out the encryption. List of options that is displayed when clicking on a certain item or area of a window in a program with the secondary mouse button usually the right.
These options are shortcuts to certain functions of a program. A window that suddenly appears, normally when a user selects an option with the mouse or clicks on a special function key. Program that is installed without express permission from the user and carries out actions or has characteristics that can reduce user control of privacy, confidentiality, use of computer resources, etc.
This is a technique used by viruses for infecting files by adding their code to the beginning of the file. By doing this, these viruses ensure that they are activated when an infected file is used. A feature in e-mail programs that allows the content of the message to be viewed without having to open the e-mail. This is the document that sets out the procedures, rules, and data security practices of a company to guarantee the integrity, confidentiality and availability of data collected from clients and other interested parties in accordance with applicable legislation, IT security needs and business objectives.
Ability to protect the computer against unknown malware by analyzing its behavior only, and therefore not needing a virus signature file periodically updated. A program that ends actions or processes that are running active on a computer, which could pose a threat. Elements that allow operations to be performed. Set of instructions, orders, commands and rules that are used to create programs. Computers understand electronic signals values 0 or 1. Languages allow the programmer to specify what a program must do without having to write long strings of zeros and ones, but using words instructions that are more easily understood by people.
A system of rules and specifications that enables and governs the communication between to computers or IT devices data transfer. A proxy sever acts as a middle-man between an internal network, such as an Intranet, and the connection to the Internet. In this way, one connection can be shared by various users to connect to an Internet server. The area next to the Windows Start button or menu, which contains shortcut icons to certain items and programs: This access could pose a threat if it is not done correctly or for legitimate purposes.
Among other things, the action by which a virus propagates or makes copies of itself, with the aim of furthering the spread of the virus. A system governing privilege levels in a microprocessor, controlling the operations that can be performed and its protection. There are various levels: Ring0 administrator , Ring1 and Ring2 administrator with less privileges , Ring3 user.
This is a type of memory which under normal circumstances cannot be written on, and therefore its content is permanent. A program designed to hide objects such as processes, files or Windows registry entries often including its own. This type of software is not malicious in itself, but is used by hackers to cover their tracks in previously compromised systems. There are types of malware that use rootkits to hide their presence on the system.
Invariable sequence of instructions, that make up part of a program and can be used repeatedly. Any illegal plot or fraud in which a person or group of persons are tricked into giving money, under false promises of economic gain trips, vacations, lottery prizes, etc.
- rastrear celular robado samsung.
- como localizar a una persona por su telefono movil gratis.
- rastreo satelital para telefono.
- Cómo saber si alguien ha instalado software de rastreo en tu computadora;
- Detección de software espía y actualidad.
- averiguar numero oculto ios.
- leer mensajes de whatsapp por voz.
This action can sometimes be considered an attack or threat. These files, which have the extension SCR, could be Windows screensavers or files written in Script language. Deja tu comentario ha ayudado a usuarios este mes. Comenta la respuesta de ShendaZ.
Espía las conversaciones de Messenger activas en tu red local
Denunciar Comenta la respuesta de gato. Comenta la respuesta de gato. Denunciar Comenta la respuesta de marlon Comenta la respuesta de marlon Denunciar Comenta la respuesta de cheison. Comenta la respuesta de cheison. Denunciar Comenta la respuesta de The Dumé. Comenta la respuesta de The Dumé.